Hackers Trick Users into Self-Infection with Fake CAPTCHA and Hidden Malware
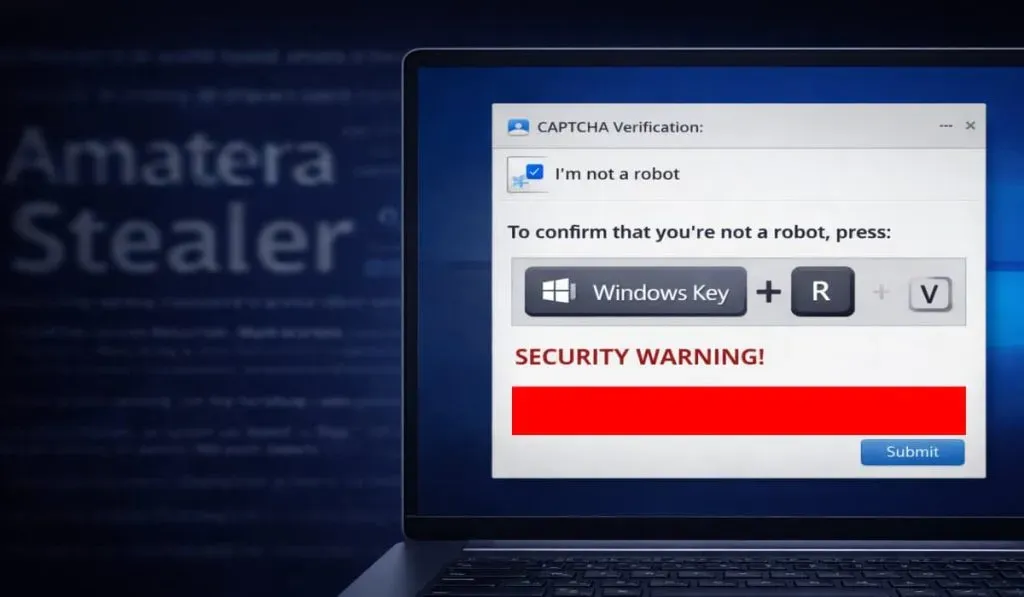
Hackers are tricking users into self-infection with a fake CAPTCHA that turns Windows own tools into a backdoor for data theft.
Blackpoint Cyber researchers Jack Patrick and Sam Decker identified a Fake CAPTCHA campaign delivering Amatera Stealer via Windows scripts and steganography. The attack uses LOLBin SyncAppvPublishingServer.vbs to bypass antivirus detection while hiding malicious code in PNG images via steganography. These manipulated images are hosted on public sites like Imgur to avoid suspicion.
The attack chain pulls instructions from a Google Calendar (.ics) file to mimic legitimate traffic patterns. Amatera Stealer specifically targets browser data, passwords, and credit card information while masquerading as traffic to microsoft.com/facebook.com.
Researchers noted this technique fails on Windows Home editions due to App-V feature requirements.
Blackpoint Cyber emphasized the threat of 'living off the land' techniques using trusted infrastructure. As Patrick and Decker explained:
This isn’t just a random set of steps. By doing this, the user is unknowingly running a command that starts the infection.




